Giving Devin Credentials
Devin can use its own login credentials to access platforms that require authentication, either in its Browser or via the command line. We recommend setting up a dedicated account for Devin to use (e.g. devin@company.com) on each service that it needs access to. You may then save Devin’s username and password as Secrets on your account, so that it can log in as part of your future sessions. Adding secrets is primarily done via the Secrets page. This page is particularly relevant for Organization-level secrets. For repo-specific or session-specific secrets, see the below sections.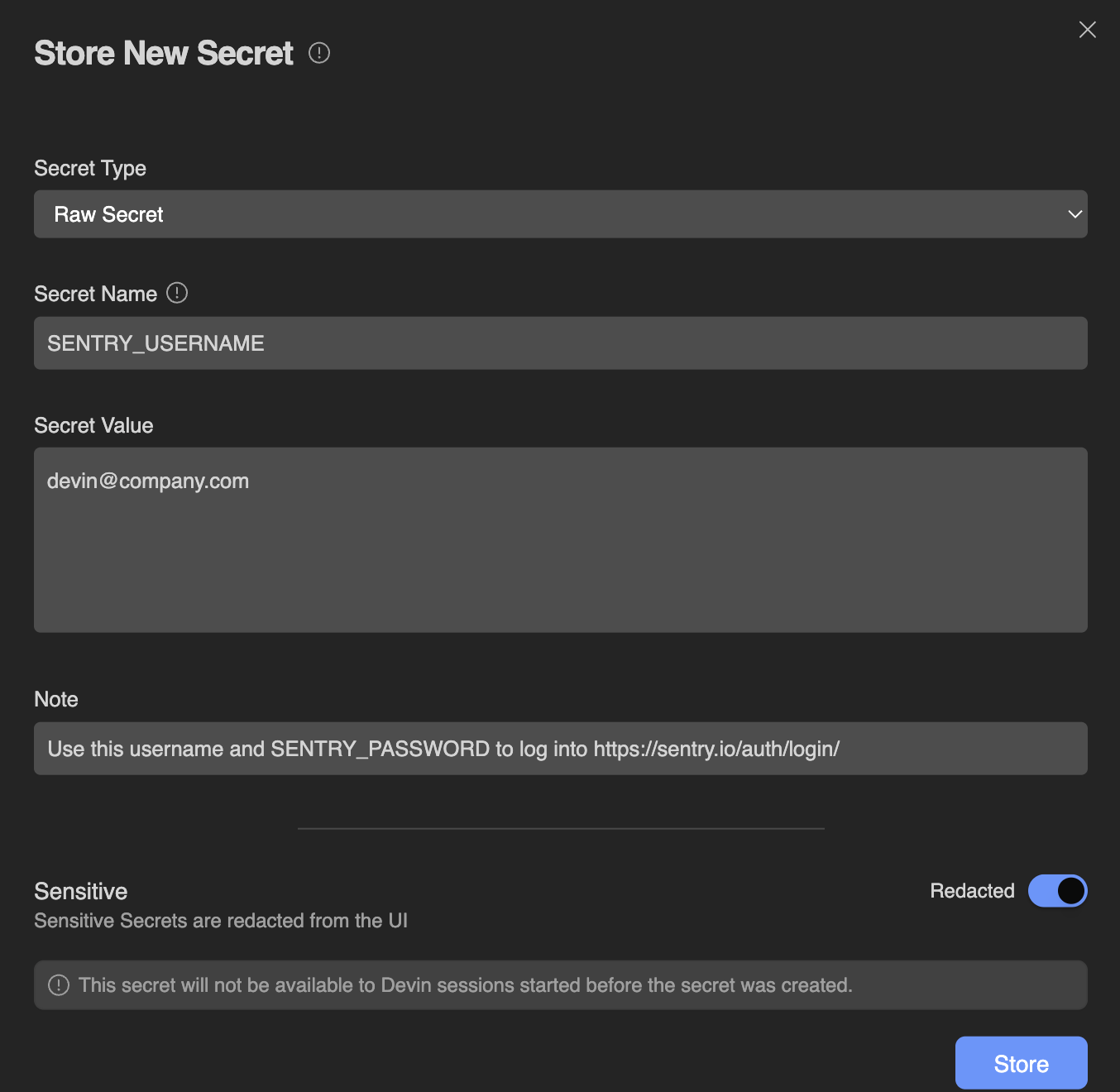
- This API key should only be used in our production env but never in staging or dev.
- Used for our AWS RDS Database in us-west-2
- These credentials are scheduled to be deprecated after Q3 2025
- Auto-expires every 30 days - ping the SecOps team for rotation if this starts failing
- This API key is attached to the devin@company.com user account
Persisted Global Secrets
Secrets added in the Settings & Library > Secrets are persisted to future sessions and apply to the entire organization. Note that any secrets you share here will be usable by Devin in all future Devin sessions within your organization. All secrets are encrypted at rest. New secrets are only available to Devin in sessions created after you added the secret. Please note that all members of your organization will be able to use Global Secrets, but only admins will be able to view or edit existing secrets. Take care to only add secrets that are specifically scoped to your organization and usable by all its members. There are a few types of secrets available:Raw Secret
Raw Secret
This is most suitable for most generic secrets with a single value. Each Secret Name (also known as a Secret Key) is associated with a single Secret Value. Examples of secrets stored here could be:
- API Keys
- SSH Keys
- Usernames or Passwords
- Tokens
Site Cookies
Site Cookies
Time-Based One-Time Password (TOTP)
Time-Based One-Time Password (TOTP)
Time-based one-time passwords are used for two-factor authentication (2FA). Devin can store TOTP secrets that act similarly to those in Google Authenticator or Authy. For details of how to add a TOTP secret, please see Adding a New TOTP
Key-Value Secrets (Deprecated)
Key-Value Secrets (Deprecated)
Devin used to support creating Key-Value secrets that would handle multiple keys per secret. However, this feature is no longer available.Instead of making key-value secrets, we recommend simply creating multiple raw secrets for each distinct field. For example, instead of creating a key-value secret for JIRA_LOGIN, you could create two raw secrets: JIRA_USERNAME and JIRA_PASSWORD.
Repo-Specific Secrets
To scope secrets to a specific repository, you can add them as environment variables (or in a .env file) during repo setup.
Session-Specific Secrets
While Devin is working, it may ask you to provide credentials (API keys, logins, etc.) within the current conversation, like so: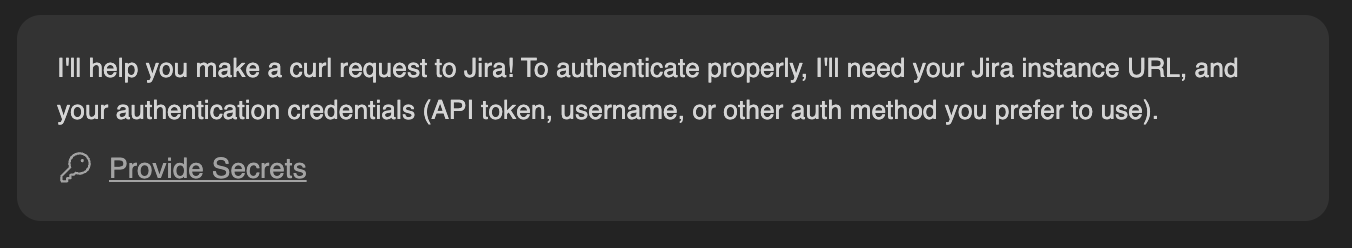
Working With Secrets
Once a secret has been configured in Devin, your application may access it like a normal ENV variable (as long as the session was started after your secret was configured). This applies to global organization-wide secrets, repo-specific secrets, and session-specific secrets. Devin performs some text conversion to ensure that your Secrets are valid ENV variables:- It removes invalid characters by replacing anything other than a letter, digit, or underscore with another underscore. For example, the secret named Abc%123 would become the ENV variable Abc_123
- If your secret name does not begin with a letter, Devin adds an underscore to the begining of the name. For example, the secret 123MYVAR would become the ENV variable _123MYVAR
- If you have two secrets with the same name, Devin will add a counter to the end. For example, if you have two secrets named MY_SECRET you would end up with two ENV variables named MY_SECRET and MY_SECRET_2 and so on.
Adding a New Site Cookie
To add a Site Cookie, please follow the steps below:- Log in as you normally would to the account you’d like to share with Devin. This will generate cookie(s).
- In order to get the cookie(s) from the browser store, download the browser extension Share your cookies and follow the steps on that Extension to extract your cookies. You may want to test that importing the cookie in another Chrome Profile successfully authenticates you to the site.
- Add the exported cookie to Devin via the Secrets page.
- When using the cookie for a site, Devin should find that it’s already logged in when it navigates to that site. Tell Devin to give it a try!
If you’re not using Chrome or need to manually encode cookies, note that Devin expects cookies in a base64 encoded string of
; delimited JSON objects in the standard chromium cookie format.One-Time Password
Devin can now handle two-factor authentication (2FA) using a time-based one-time password (TOTP). To do this, you’ll need to give Devin the information provided at the time 2FA is set up on Devin’s account for the specific application:- Access Devin’s account for the service that requires 2FA.
- Go to the account security settings and look for an option to regenerate or view the QR code. This may be called Set up or Replace Authenticator.
- If the application allows, select the option to view the QR code.
- Once the QR code is displayed on your screen, take a screenshot.
- Go to Devin’s Secrets, click on the “Add Secret” button, and change the Secret type to “One-time Password”. Put a descriptive name. Click the small QR code icon in the top right of the Value input box and upload your QR code screenshot.
Tips for TOTPs
- Some applications may not allow you to view the existing QR code once 2FA is enabled. In such cases, regenerating the QR code is the only option.
- Always save any new backup codes provided during the process in a secure location.
