Why integrate Devin with GitHub?
Integrating Devin with your GitHub organization enables Devin to create pull requests, respond to PR comments, and collaborate directly within your repositories. This allows Devin to function as a full contributor on your engineering team. To get started, navigate to app.devin.ai > Settings > Integrations > GitHub, click Add Connection, and follow the prompts. You will select which repositories Devin can access and review the required permissions.Using GitHub Enterprise Server? See the GitHub Enterprise Server Integration guide for setup instructions using personal access tokens.
Setting up the Integration
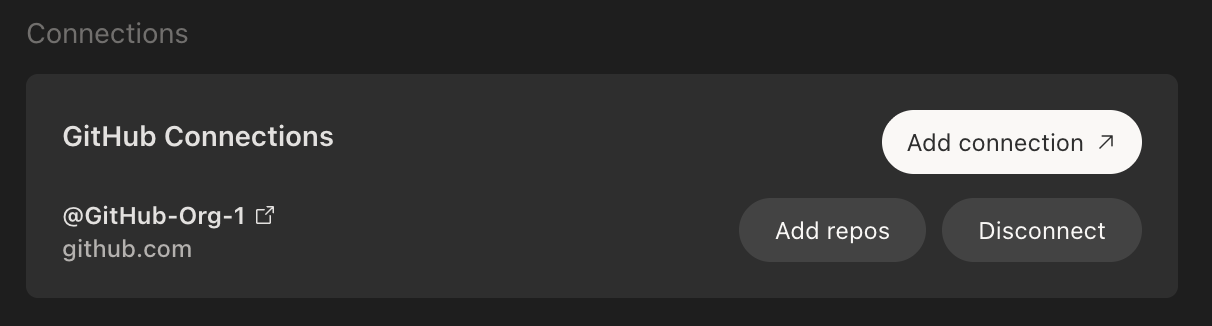
- In your Devin account at app.devin.ai, navigate to Settings > Integrations > GitHub and click Add Connection.
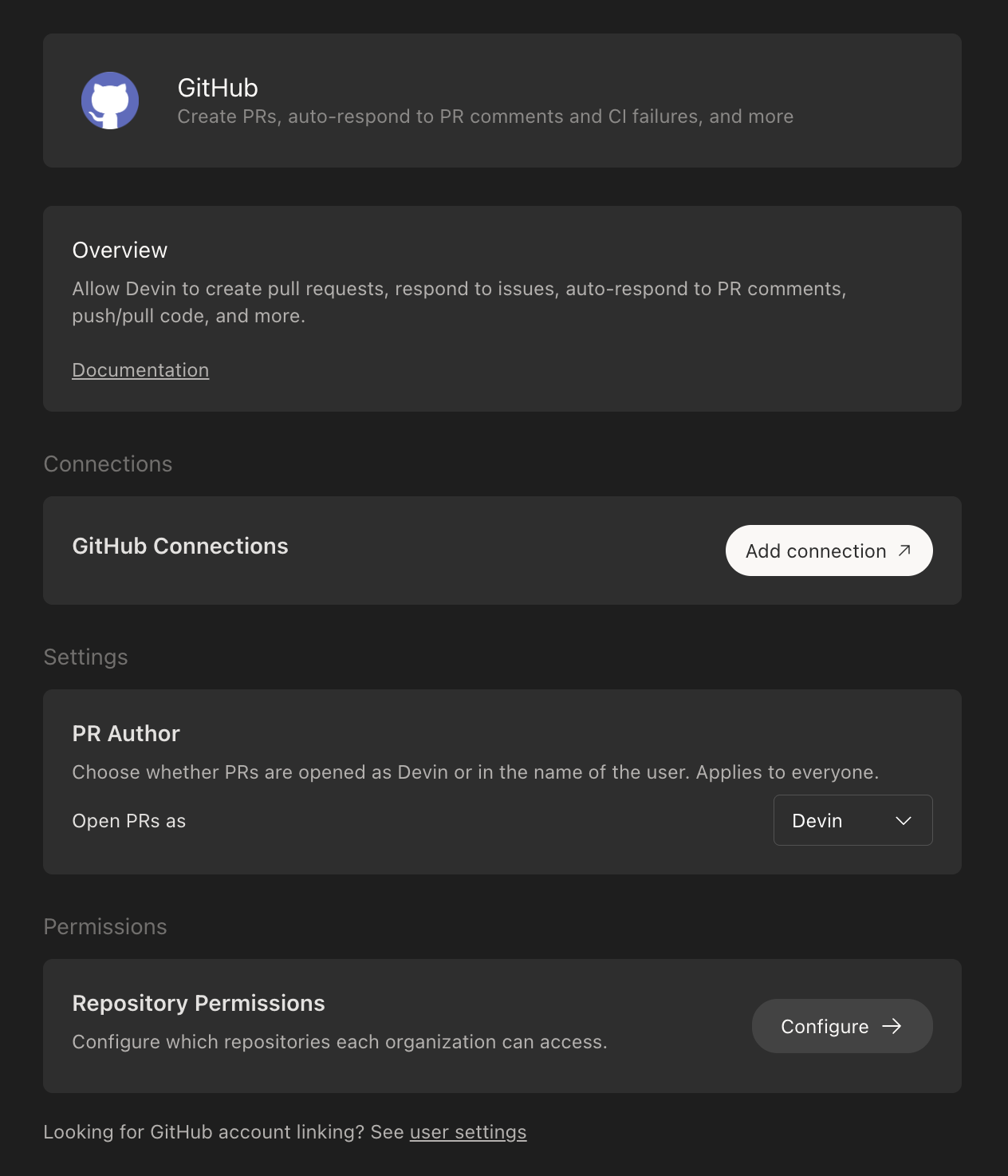
- If you are not already logged in to GitHub, you will be prompted to authenticate.
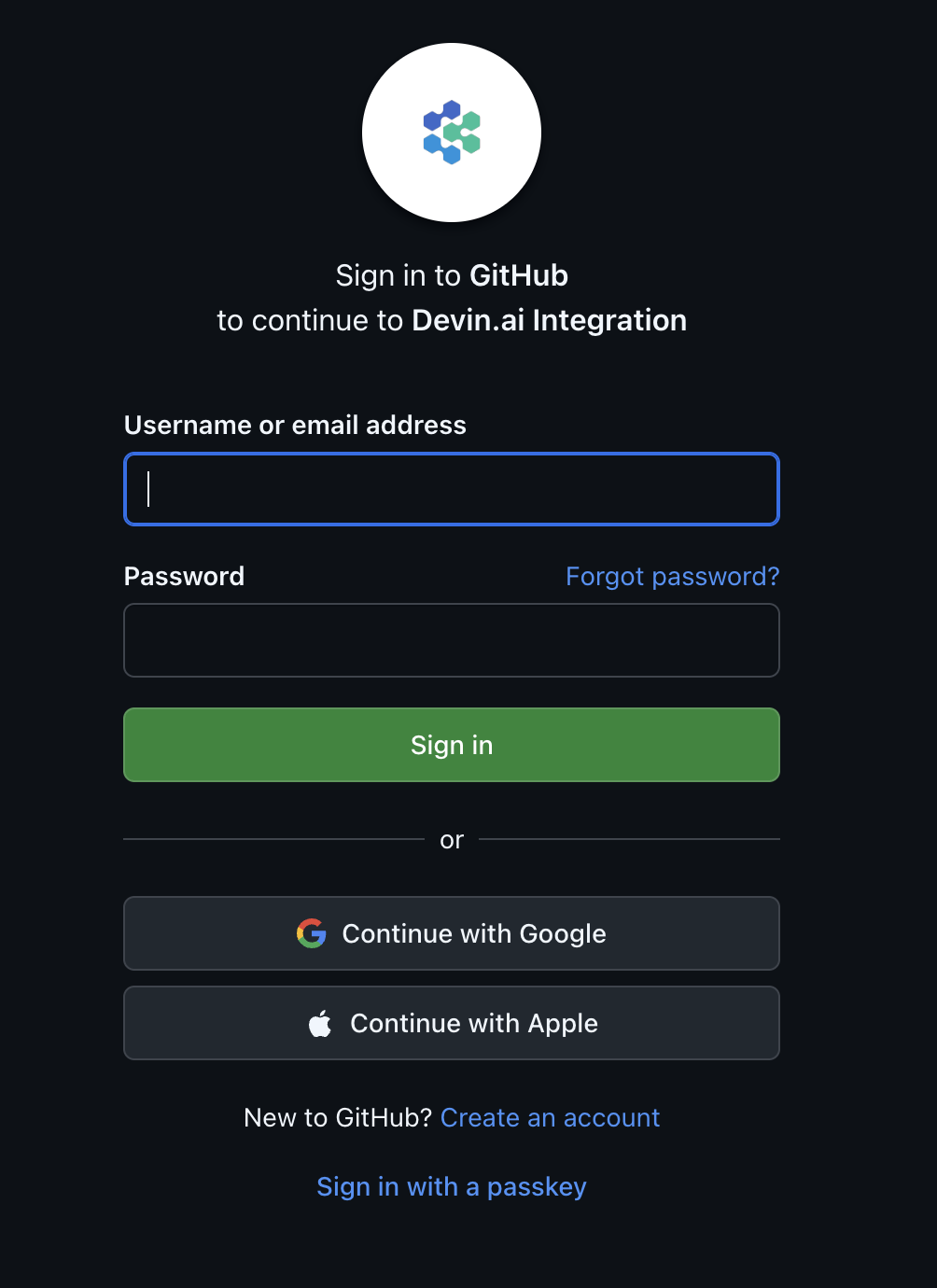
- Select the GitHub organization you want to connect to Devin.
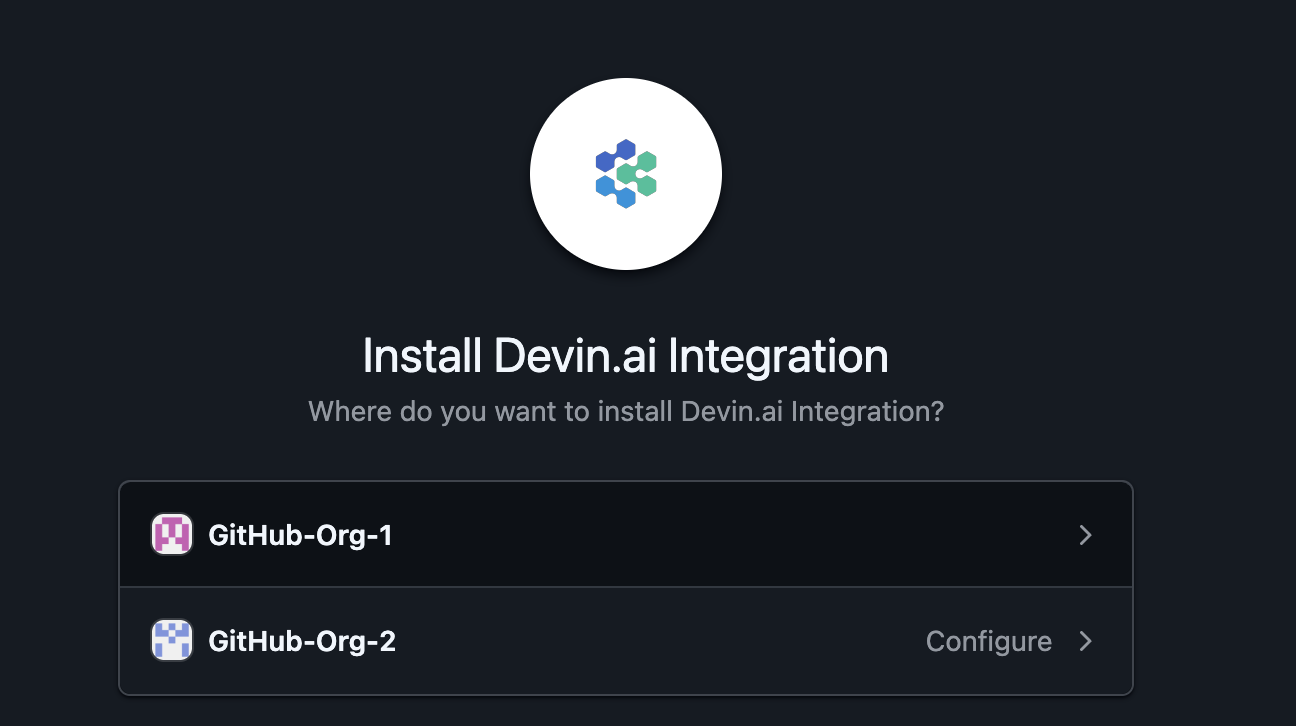
- Choose whether to grant Devin access to All repositories or Select repositories to control which repositories Devin can access.
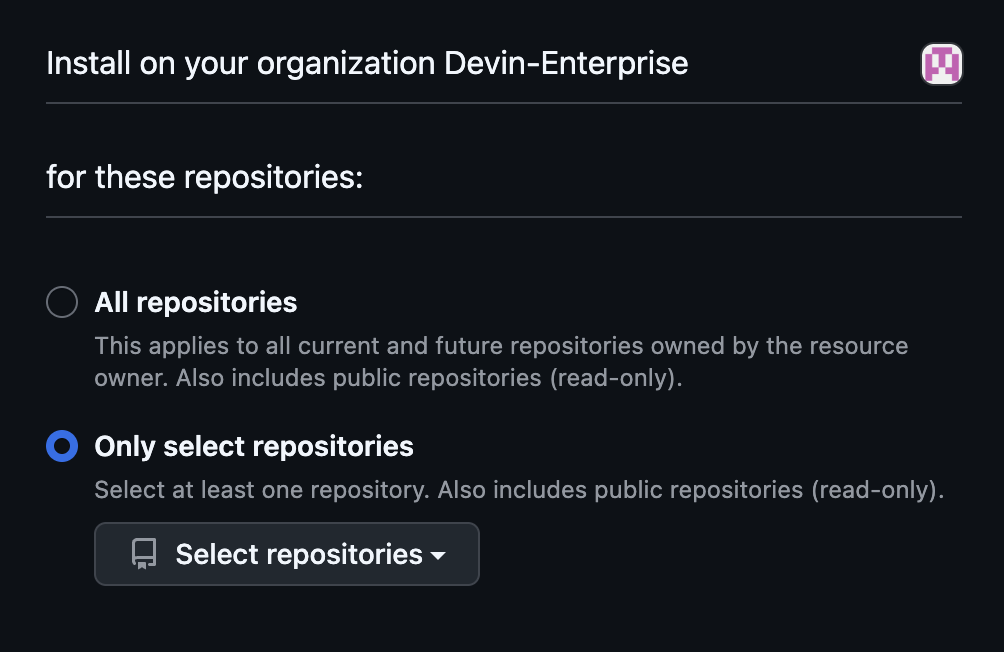
- After completing the GitHub authorization, you will be redirected to Devin settings where you can confirm the integration is active.
Using Devin with the GitHub Integration
For Core and Teams users
Once the integration is configured, you can @mention repositories directly in your prompts within the Devin web application.For Enterprise users
Once the integration is configured, you can delegate repositories to specific organizations from Enterprise Settings > Repository Permissions.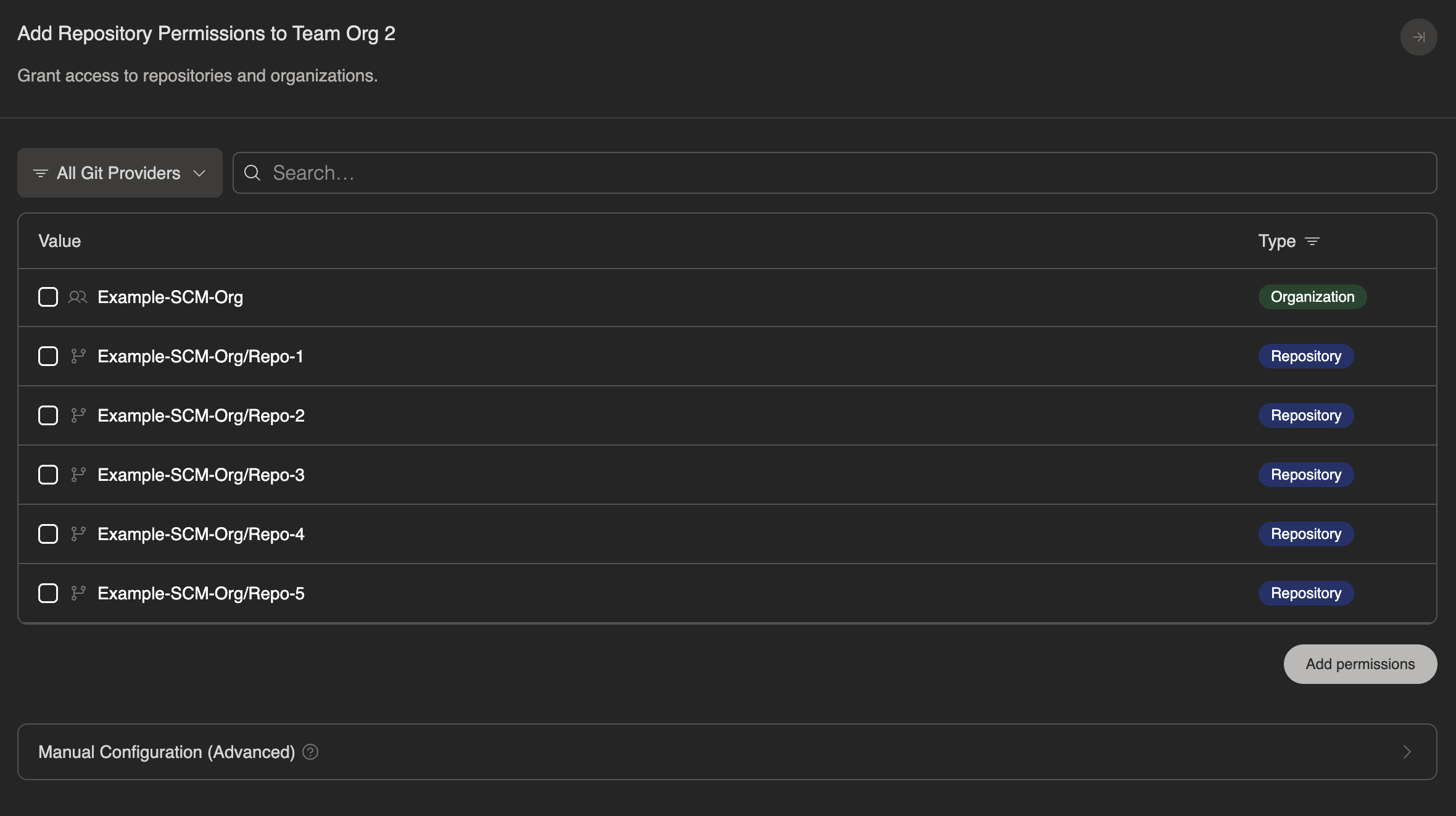
Managing Devin’s Permissions in GitHub
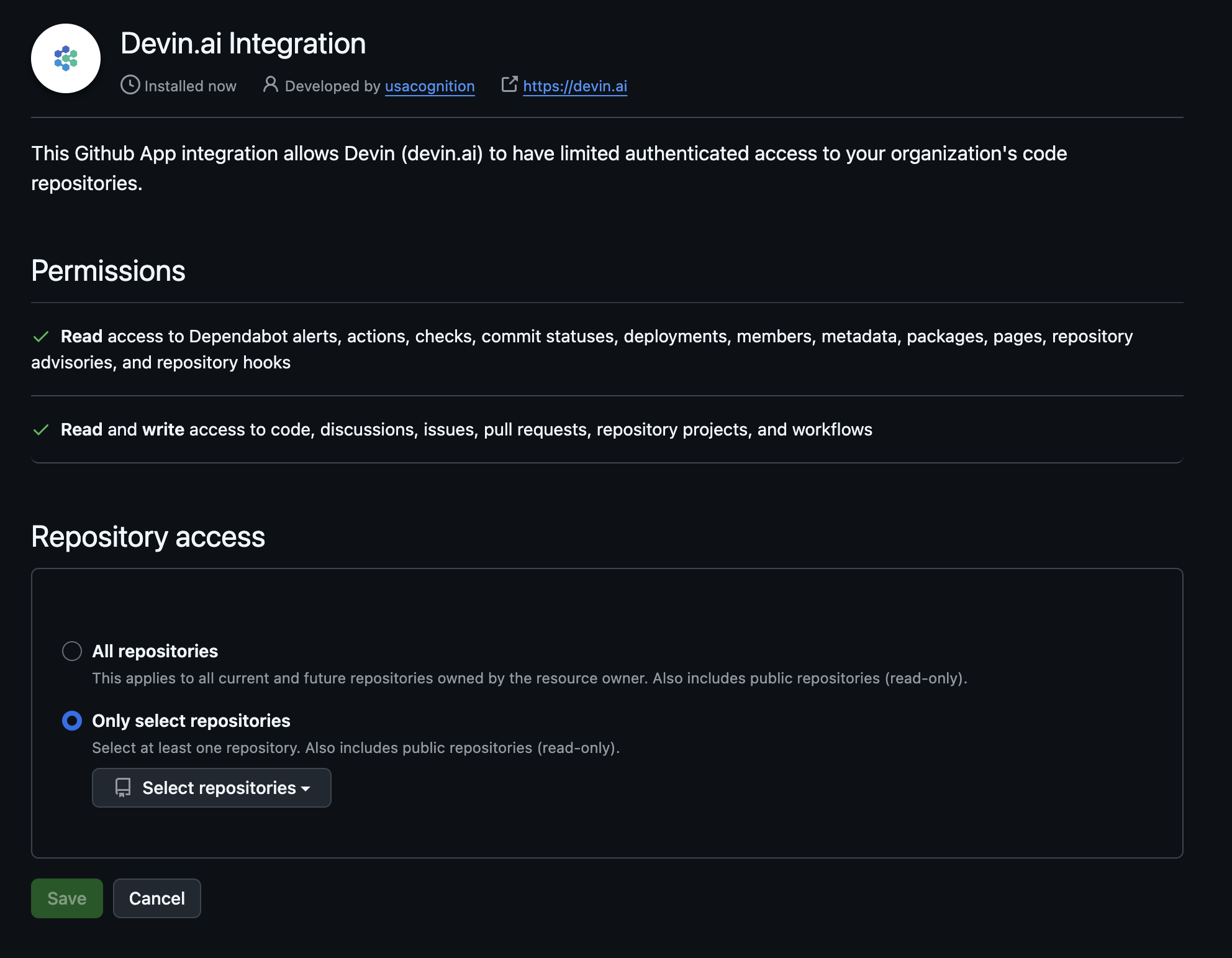
During setup, you can grant Devin access to all repositories in your organization or limit access to specific repositories. You can adjust repository access at any time through GitHub’s settings:- Navigate to your GitHub organization’s Settings > GitHub Apps (e.g.,
https://github.com/organizations/<org_name>/settings/installations) - Select Configure for the Devin.ai integration
- Under Repository access, choose to grant access to all repositories or select specific repositories
- Click Save to apply your changes
| Permission | Description |
|---|---|
dependabot alerts | Allows Devin to resolve dependabot alerts on your behalf (i.e. bumping dependency versions) |
actions | Allows Devin to view the actions configured for a repository in order to understand if Devin’s changes pass CI |
deployments | Allow Devin to view which versions of a repository were deployed |
metadata | Allow Devin to view crucial metadata about a repository such as who owns it |
packages | Allow Devin to view which versions of a repository were shipped as a package |
pages | Allow Devin to consult pages associated with a repository, e.g. to view documentation |
repository security advisories | Allow Devin to view security advisories related to a repo in order to help fix security issues |
members | Allow Devin to view members of an organization |
webhooks | Allow Devin to view the hooks configured for a repository, e.g. linting and type checking |
| Permission | Description |
|---|---|
checks | Allows Devin to view and report check results for a repository in order to understand and communicate if Devin’s changes pass CI |
commit statuses | Allow Devin to view and set commit statuses to indicate if a commit passes CI |
contents | Allow Devin to contribute to the codebase |
discussions | Allow Devin to contribute to discussions |
issues | Allow Devin to open new issues |
pull requests | Allow Devin to create new PRs |
projects | Allow Devin to view and manage projects associated with a repository, e.g. to retrieve information about a task |
workflows | Allow Devin to set up new workflows, e.g. to help configure CI/CD |
Pull Request Templates
When Devin creates a pull request, it uses a template from your repository to structure the PR description. If you provide a template, Devin follows its format when submitting PRs to GitHub.Devin-specific template (recommended)
You can provide Devin with its own template without modifying your default human-facing template by adding a file nameddevin_pr_template.md in one of the supported PULL_REQUEST_TEMPLATE locations below. This is useful if you want Devin to include additional context, such as a reviewer checklist or a Mermaid diagram of modified files.
Template search order
Devin searches for templates in the following order and uses the first match:- PULL_REQUEST_TEMPLATE/devin_pr_template.md
- docs/PULL_REQUEST_TEMPLATE/devin_pr_template.md
- .github/PULL_REQUEST_TEMPLATE/devin_pr_template.md
- pull_request_template.md
- docs/pull_request_template.md
- .github/pull_request_template.md
For more on GitHub pull request templates (supported locations, multiple templates, query parameters, etc.), see the GitHub Docs: Creating a pull request template for your repository.
Commit Signing
During repository setup, you can use Devin’s terminal to generate a GPG key for signing commits, following the process outlined in GitHub’s documentation. We recommend creating a dedicated GitHub account in your organization (e.g., devin@company.com) to associate with the GPG key, making it easy to identify commits from Devin.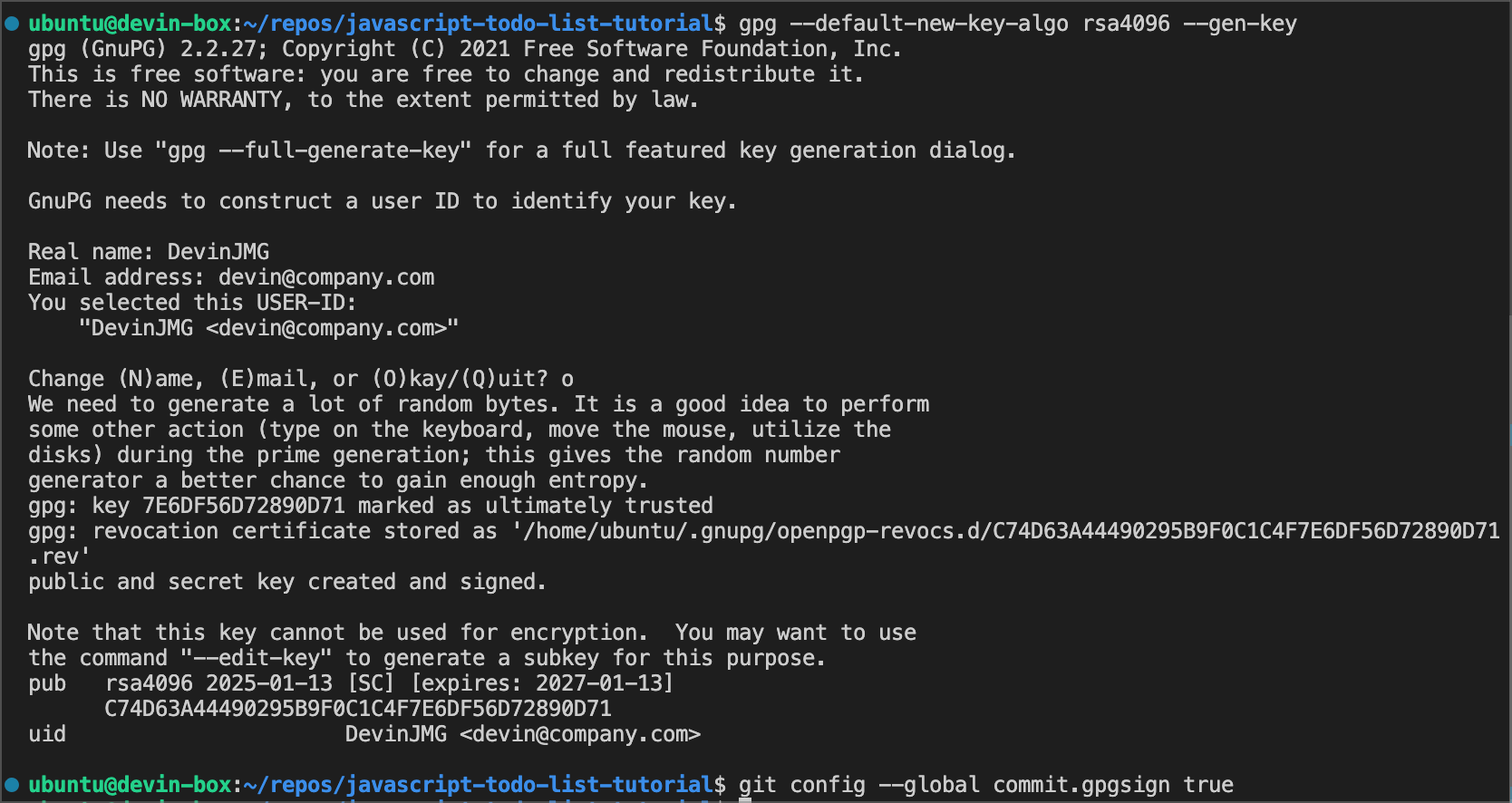
Security Considerations
- Branch protection: We recommend enabling branch protection rules on your main branch to ensure all required checks pass before Devin can merge changes.
- Organization-level permissions: Devin uses the permissions granted at the organization level, not the permissions of the individual user running a session.
- Consistent access: All users with access to both the GitHub and Devin organizations share the same Devin integration permissions.
- Repository creation: Devin cannot create new repositories in your GitHub account.
IP Allowlisting
If your organization requires IP allowlisting for GitHub access, add the following IP addresses:- 100.20.50.251
- 44.238.19.62
- 52.10.84.81
- 52.183.72.253
- 20.172.46.235
- 52.159.232.99
These IP addresses may change in future updates. We recommend monitoring our release notes for any changes.
GitHub Integration FAQs
Can I connect a personal GitHub account to my organization's Devin account?
Can I connect a personal GitHub account to my organization's Devin account?
Yes, you can connect either a GitHub Organization or a personal GitHub account to your Devin organization. However, we recommend connecting the account that has the appropriate permissions for Devin to access the repositories your team needs.
How does the GitHub app handle user authentication?
How does the GitHub app handle user authentication?
Only users who are members of the organization that installed the GitHub integration can use it in their Devin sessions. Devin inherits access to the GitHub integration based on the user’s organization membership.
How does Devin manage and rotate encryption keys?
How does Devin manage and rotate encryption keys?
Encryption keys are managed by AWS KMS and rotated periodically.
