Devin Azure VPC Deployment Guide
This guide outlines the process for deploying Devin in your Azure Virtual Private Cloud (VPC) environment, providing access to resources within your corporate firewall.- Simple Setup (Terraform)
- Advanced Setup (Manual)
Terraform Deployment (Recommended)
Terraform deployment is our recommended approach for setting up Devin in your Azure VPC. This automated method ensures consistent, repeatable infrastructure provisioning with minimal manual configuration.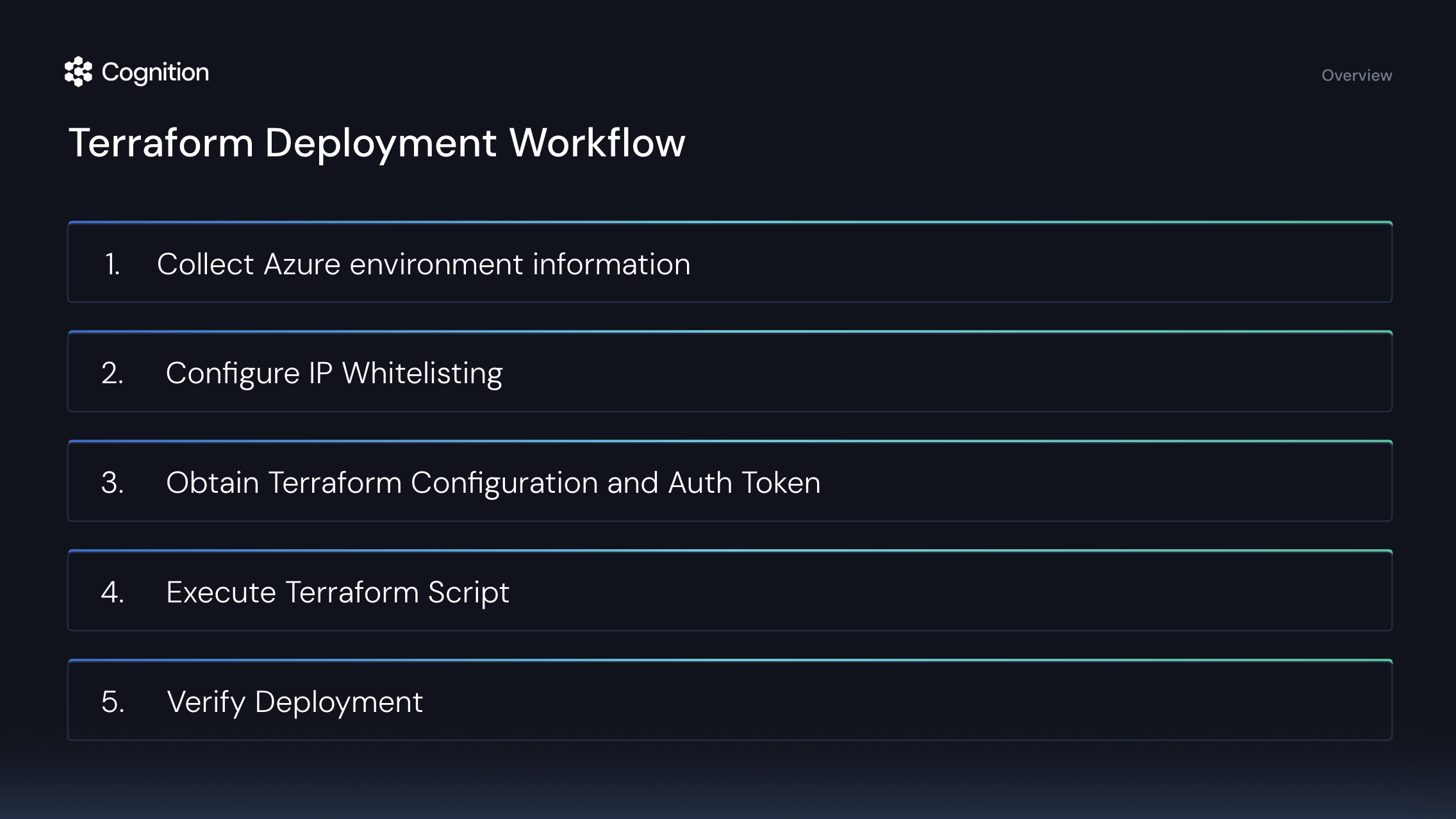
Prerequisites
Before beginning the Terraform deployment process, ensure you have:- Setup VPC for Devin (either use an existing VPC or provision a new one)
- Ensure you have an Azure account with permissions to:
- create virtual machines
- create storage accounts in your region
- Ensure your Azure account can support instances with at least 70 virtual CPUs
- Terraform (version 1.0 or later) installed
Step-by-Step Deployment Process
Collect Azure Environment Information
Gather the following information which will be required for the Terraform configuration:
- Azure Subscription ID (GUID format)
- VPC ID (Virtual Network name)
- Two Subnet names:
- subnet-1
- subnet-2
Configure Firewall Access
- User Device Firewall
- VPC Firewall
Ensure your endpoint security systems (user devices that will access Devin) allow access to:
- *.devin.ai
- *.devinenterprise.com
- *.devinapps.com
Obtain Terraform Configuration and Auth Token
Contact Cognition to receive:
- An authentication token for pulling the hypervisor image
- The Terraform configuration files customized for your environment
Execute Terraform Script
We can schedule a call to execute this step together. The process involves:
-
Extract the Terraform configuration files to a directory on your local machine:
-
Initialize the Terraform environment:
-
Review the planned infrastructure changes:
-
Apply the configuration to provision the infrastructure:
- Confirm the changes when prompted.
The Terraform scripts will set up all necessary components including virtual machines, storage accounts, security groups, IAM roles, and the hypervisor registration.
Run First Devin Session
After the Terraform script completes successfully, we will work together to:
- Verify that the resources have been created in your Azure portal
- Run a first Devin session to ensure connectivity to the required services
- Debug any issues that arise with the support of Cognition team